Using TMeter as firewall
Although TMeter, promoted as traffic monitoring
software, is typically used in conjunction with a separate
firewall, it has the capability to deny network packets because it
is built on a firewall engine.
Let's consider a typical case for creating a firewall solution
using TMeter. For example, we have an office network whose gateway
runs Windows Server 2003, with Routing enabled and Remote Access
Service (RRAS) playing the NAT-router role.
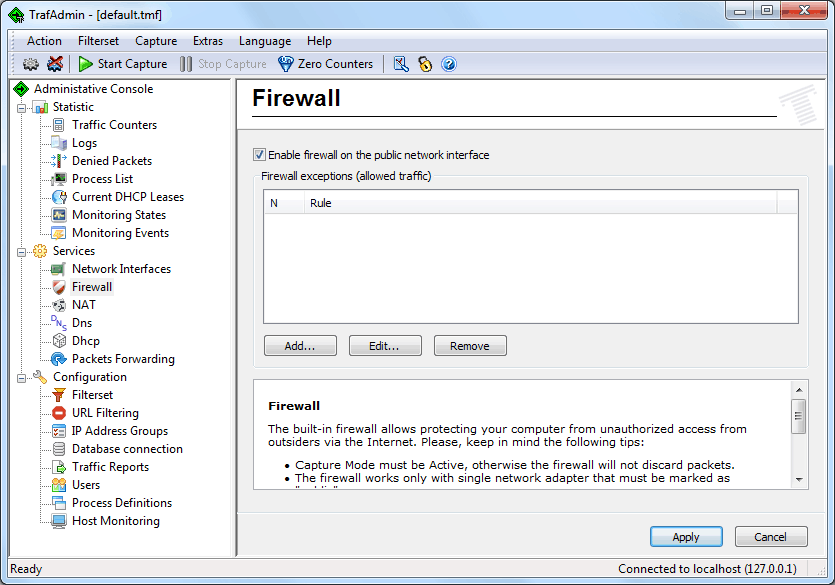
What packets should be denied to defend the gateway against
hackers? A solution would be to restrict access to all network
services on the gateway from any untrusted networks. This goal can
be reached when you enable firewall on the public interface.
Stateful Inspection technique
TMeter firewall is not simple packet-filtering engine. The firewall has "Stateful Inspection" feature which significally increases overall security. If you access some outside service, the server remembers things about your original request like port number, and source and destination address. This "remembering" is called saving the state. When the outside system responds to your request, the firewall server compares the received packets with the saved state to determine if they are allowed in.

 Note
Note